
CSCI E-180 Calendar - Spring 2006

History of user interfaces, from plug boards to modern mouse-and-window systems. UIs for cell phones. The web as a GUI; the web as remote procedure call.
Events; Model-View-Controller; Windows; Widgets; Focus; Selection. Examples from MacOS Cocoa and Qt.
Theus, Martin, "User Interfaces of Interactive Statistical Graphics Software." in Computer Science and Statistics, Proceedings of the 31th Symposium on the Interface 1999.
Gentner, Don, and Nielson, Jakob. "The Anti-Mac Interface" CACM, August 1996, pp. 70-82
Part V: Mice and Manipulation, in About Face 2.0: The Essentials of Interaction Design, Alan Cooper & Robert Reimann, 2003.
The Anti-Mac Interface - KDE User Interface Guidelines
http://developer.kde.org/documentation/design/ui/antimac.html
DigiBarn Systems: Canon Cat
http://www.digibarn.com/collections/systems/canon-cat/page_01.htm
2.10: Canon, Lone Wolf
http://www.wired.com/wired/archive/2.10/canon_pr.html
The UI Hall of Shame
Documentation:
Discussion: Mac vs. Anti-Mac.
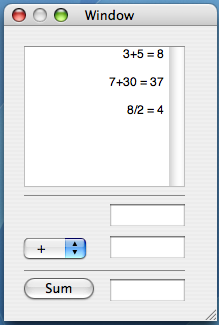
Using the interface toolkit of your choice, create a simple calculator with the following: Two text fields to enter two numbers, a pull-down (or pop-up) menu that selects the operation, a third text field for the result, a button that makes the calculator perform the operation, and a "tape roll" that shows the results of previous calculations. Bring to class a printout with your code and another printout with screenshots.
Here is a sample screen shot:
Gentner, Don, and Nielson, Jakob. "The Anti-Mac Interface" CACM, August 1996, pp. 70-82
Today's class will be devoted to conducting informal usability reviews.
Ideas for Project 1:
Part I: Bridging the Gap, in About Face 2.0: The Essentials of Interaction Design, Alan Cooper & Robert Reimann, 2003.
Neilsen, Jakob. "Guerrilla HCI: Using Discount Usability Engineering
to Penetrate the Intimidation Barrier," 1994.
Guerrilla HCI
http://www.useit.com/papers/guerrilla_hci.html
Nielsen, Jakob. "Iterative User-Interface Design," IEEE Computer, November 1993 (Vol. 26, No. 11), pp. 32-41. Download from the class website.
Part II: Achieving Goals and Removing Barriers, in About Face 2.0: The Essentials of Interaction Design, Alan Cooper & Robert Reimann, 2003.
Norman, A. "Design Rules based on Analyses of Human Error." Communications of the ACM, April 1983.
Quan, D., Bakshi, K., Huynh, D., and Karger, D. User Interfaces for Supporting Multiple Categorization, Interact 2003.
Building a client/server app; Berkeley Sockets; Marshalling; XML RPC; SOAP; SSL; Peer-to-peer systems.
Part II: Achieving Goals and Removing Barriers, in About Face 2.0: The Essentials of Interaction Design, Alan Cooper & Robert Reimann, 2003. (finish this and bring the book to class; we will discuss it.)
Lansdale, M., The psychology of personal information management," Applied Ergonomics 1988, 19.1, 55-66
Grudin, Jonathan, The Case Against User Interface Consistency," CACM, October 1989
Chord: A Scalable Peer-to-peer Lookup Service for Internet Applications , Ion Stoica, Robert Morris, David Karger, M. Frans Kaashoek, and Hari Balakrishnan, In the Proceedings of ACM SIGCOMM 2001, San Deigo, CA, August 2001.
WebOS: Say Goodby to Desktop Applications
Data Caching Issues in an Information Retrieval System, Rafael Alonso et al., ACM Transactions on Database Systems, 1990.
Dojo - DojoToolkit.org
http://dojotoolkit.org/
OpenLaszlo | the premier open-source platform for rich internet applications
http://www.openlaszlo.org/
TIBCO General Interface™ Resource Center
http://www.tibco.com/software/business_optimization/gi_resource_center.jsp
Remote Scripting with AJAX part1 and part2, by Cameron Adams, XML.COM, August 2005.
Latency Must Die: Reducing Latency by Preloading Data
http://www.jonathanboutelle.com/mt/archives/2004/08/latency_must_di.html
Ajax Blog - HTML, Javascript and XML coding techniques for Web 2.0
http://ajaxblog.com/
The Last Craft? Marcus' blog on Agile Web Development » Listen kids, AJAX is not cool
http://www.lastcraft.com/blog/index.php?p=19
SitePoint Blogs » AJAX@localhost
http://www.sitepoint.com/blogs/2006/02/10/ajaxlocalhost/
AJAX:Getting Started - MDC
http://developer.mozilla.org/en/docs/AJAX:Getting_Started
Ajax & XmlHttpRequest
http://www.xul.fr/en-xml-ajax.html
Software Secret Weapons: Javascript Refactoring For Safer Faster Better AJAX
http://www.softwaresecretweapons.com/jspwiki/Wiki.jsp?page=JavascriptRefactoringForSaferFasterBetterAJAX
Main Page - Ajax Patterns
http://ajaxpatterns.org/
Mastering Ajax, Part 1: Introduction to Ajax
http://www-128.ibm.com/developerworks/java/library/wa-ajaxintro1.html
Mastering Ajax, Part 2: Make asynchronous requests with JavaScript and Ajax
http://www-128.ibm.com/developerworks/java/library/wa-ajaxintro2/index.html
Mastering Ajax, Part 3: Advanced requests and responses in Ajax
http://www-128.ibm.com/developerworks/java/library/wa-ajaxintro3/index.html
Your first project is to develop a working application that demonstrates some aspect of graphical user interface design and interaction that we have discussed during this class. Your turned in work should consist of the following:
We would prefer it if you would put all of this information on a web page and email us the URL. Please also let us know if we may post your URL to the class. If you wish for your submission to be private, please feel free to put your project on a password-protected website. If you do not have access to such a website, please bring your project to class on a CDROM. (Please bring two copies of the CDROM, one for the teacher, one for the TF.)
Harvard KB0032 discusses how FAS accounts can be used to webhost.
How to build a file synchronizer.
Part III: Providing Power and Pleasure, in About Face 2.0: The Essentials of Interaction Design, Alan Cooper & Robert Reimann, 2003.
Cookie Authentication. Hidden URL's. Apache .htaccess. httpd file step through.
Andrew Tanenbaum, Sape Mullender, and Robbert van Renesse. Using sparse capabilities in a distributed system. In Proceedings of the 6th International Conference on Distributed Computing, pages 558-563, Cambridge, MA 1986. [CiteSeer]
What encryption is, and how it works. Providing for local secure storage. Secure transportation of data over a network. Spyware.
Good, Nathaniel S., Krekelberg, Aaron, Usability and privacy: a study of Kazaa P2P file-sharing
Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy. A Crawler-based Study of Spyware on the Web. Proceedings of the 13th Annual Network and Distributed System Security Symposium (NDSS 2006), San Diego, CA, February 2006.
Accessibility for non-traditional devices and non-traditional users. HDML and WAP. Java on a cell phone. Screen readers. Tactile interfaces. Computing for the blind.
Raskin, Will Computers Ever Become Easy to Use, Communications of the ACM, Volume 40, No. 2, February 1997.
Ludi, Access for Everyone: Introducing Accessibility Issues to Students in Internet Programming Courses. , 32nd ASEE/IEEE Frontiers in Education Conference, November 6-9, 2002. Boston, MA.
Eleanor T. Loiacono, Cyberaccess: Web Accessibility and Corporate America, Communication of the ACM, December 2004
Hull, Larry. Accessibility: It's not just for disabilities anymore. interactions. March+April 2004
Coding Standards. Plug-ins. Checkpointing.
Representing time inside a program. Time zones. Handling multiple charactersets and languages. Unicode.
iCalendar files. Synchornizing clocks.
Beck, Roy. "How do you Set the Time on your VCR?" The San Gabriel Valley Technology User's Group, June 2001.
Crazy Clocks: Counterintuitive Consequences of "Intelligent" Automation. IEEE Intelligent Systems, November/December 2001 ,pp. 74-76
iCalendar spec
Very large regular expressions; Spell Checking;
Peterson, Computer Programs for Detecting and Correcting Spelling Errors, Communications of the ACM, Volume 23, Number 12. December 1980
Durham, Lamb and Saxe, "Spelling Correction in User Interfaces Communiations of the ACM, October 1983.
Galletta, Durcikova, Everard, and Jones, "Does Spell-Checking Software Need a Warning Label?" Communications of the ACM, Vol 48, No. 7, July 2005.